How to tell if your technology service provider uses best practices to ensure the privacy of your data.
As transactions go online and more data is stored in the cloud, protection of sensitive information like credit card numbers and passwords becomes more important. Data breaches can result not only in lawsuits and bad PR, but significant fines as well.
- In December 2006, TJX companies discovered credit card numbers for 45 million customers were stolen and used to open fake credit card accounts. Settlements to multiple lawsuits were estimated to be between $250 and $500 million.
- According to the USITC, Google was fined $56M by French authorities after finding Google’s use of blanket consent forms and pre-ticked boxes are not sufficient as valid and clear consent under GDPR.
- Similarly, since implementation of GDPR by the EU, Europe has imposed more than $400 million in fines. Litigation continues against FaceBook, Instagram, Twitter, LinkedIn, Apple, Google and Verizon.
We know data privacy is a big deal, but what are the guidelines and regulations that define good practices?
The European Union created the General Data Protection Regulation (GDPR) in 2018 which has become the gold standard for protecting individuals’ information. Under GDPR the user “owns” their data. For a company to utilize the customer data, there must be “informed and affirmative” consent. Users have the power to require companies to change the data, provide a copy, and erase data. GDPR applies to organizations operating in the EU and organizations outside the EU that do business in the EU. Fines for violations are up to 20 million euros or 4% of annual revenue/turnover, whichever is greater.
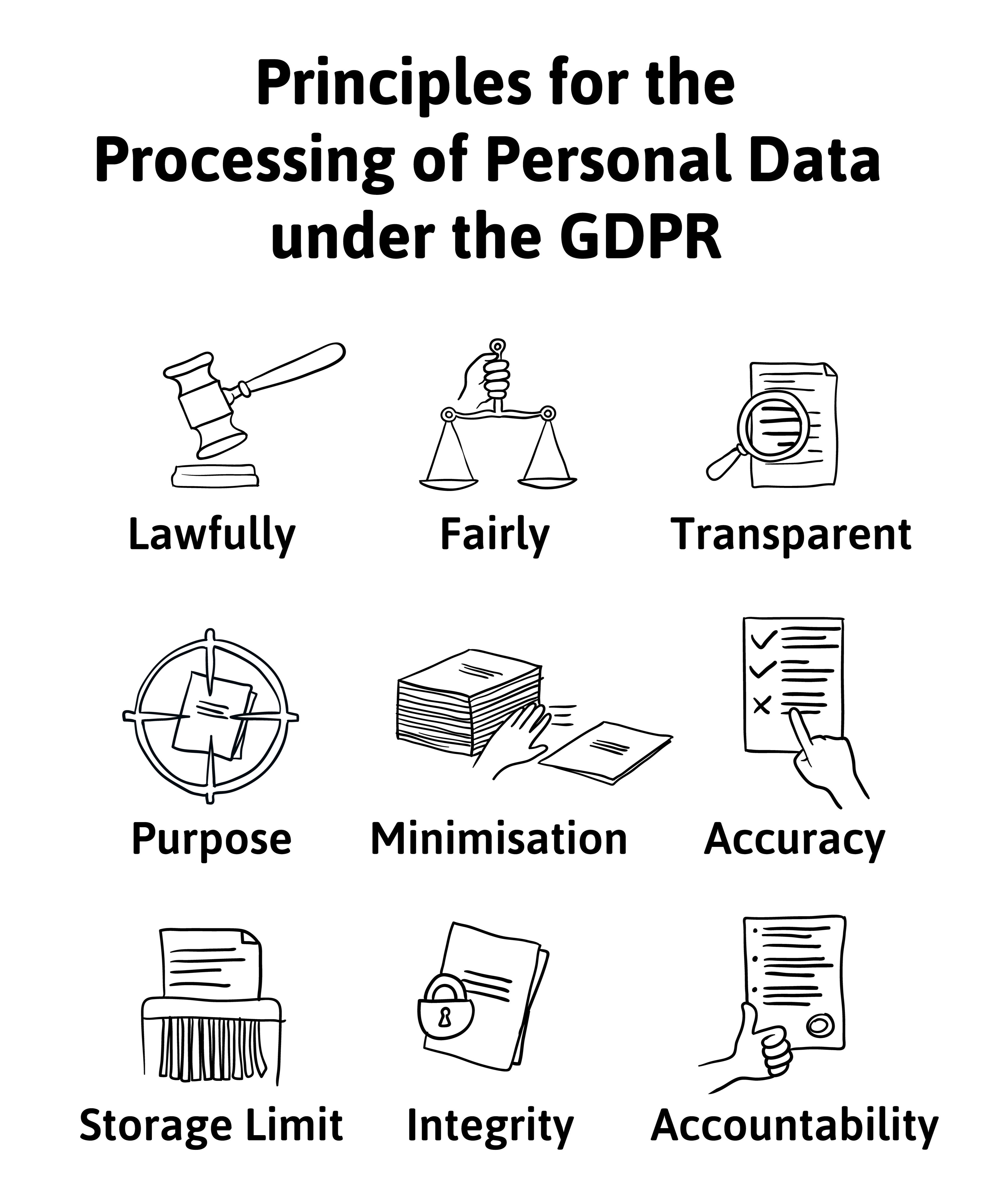
Regulations in the US are more of a patchwork of Federal, State and Common Law. Historically, Federal laws like HIPPA (Healthcare Insurance Portability Accountability Act) and GLBA (Gramm-Leach-Bliley Act) protect individuals’ healthcare and financial information respectively. While bills to address data protection make their way through the US House and Senate, California instituted its own set of requirements that took effect January 2020.
The CCPA (California Consumer Privacy Act) provides California residents with the ability to control how businesses process their personal information. Businesses will now have to honor requests from California residents to access, delete, and opt out of sharing or selling their information. Additionally, businesses will have to consider a number of CCPA-specific requirements when updating their privacy programs, such as the CCPA’s prescriptive opt-out measures, and the need to stop selling consumer data upon an individual’s request.
The CCPA applies to for-profit businesses that collect and control California residents’ personal information, do business in the state of California, and meet at least one of the following thresholds:
- Annual gross revenues larger than $25 million
- Receive or disclose the personal information of 50,000 or more California residents, households, or devices each year
- Make 50 percent or greater annual revenue from selling California residents’ personal information

Unlike GDPR and CCPA which are legislative acts enforceable by law, SOC 2 is another type of data protection that takes the form of criteria evaluated in an audit. Compliance with SOC 2 can get a company far down the path of GDPR compliance. SOC 2 is broken down into the following 5 trust principles:
- Security: protection of system resources against unauthorized access.
- Availability: accessibility of the system, products, or services as stipulated by a contract or service level agreement (SLA)
- Processing Integrity: addresses whether a system achieves its purpose (i.e., delivers the right data at the right price at the right time).
- Confidentiality: Data is considered confidential if its access and disclosure is restricted to a specified set of persons or organizations.
- Privacy: the system’s collection, use, retention, disclosure, and disposal of personal information in conformity with an organization’s privacy notice, as well as with criteria set forth in the AICPA’s generally accepted privacy principles (GAPP).
AiRISTA is in the process of conducting a SOC 2, Type I compliance audit to reassure our clients their data and privacy are protected. This audit, aligned with our hosting partner Amazon Web Services who is certified for SOC 3, will position AiRISTA with further compliance objectives and certifications. A copy of AWS’ SOC 3 report can be found here SOC 3 Report, and additional compliance information is located at AWS Compliance Site.
AiRISTA has a long history of commitment to privacy of personal information. With over 10 years of experience in markets that require stringent data protection, we welcome efforts that create a common criteria. AiRISTA complies with GDPR, CCPA and soon to be SOC 2 compliant. For our GDPR and CCPA privacy notice, see the following:





